Intigriti's April Challenge 2023 Writeup
This write-up details my solution to Intigriti’s April challenge by strangeMMonkey1. I will focus solely on the steps I took to solve the challenge, though it’s worth noting that I was stuck in some moments looking rabbit holes. I believe I was among the first ten person’s to successfully solve the challenge.

The challenge starts with a login page (/challenge.php) in which you can use the credentials 'strange:monkey' that appears in the page. If you try to use other credentials, you get redirected to an error page (/index_error.php?error=blabla). While the XSS in the URL parameter is noteworthy, the real significance of this page lies in the comment embedded in the HTML. This comment mentions strict comparisons. If you have some CTF or PHP dev background, you will immediately think about the bug of PHP comparison called type juggling (explanation) (payloads).
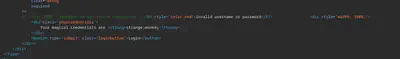
Although I initially attempted to exploit a type juggling bug on the login page, I eventually discovered that the actual bug was in the cookie that was set after logging in with the provided credentials.
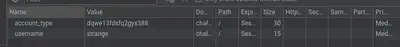
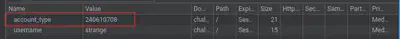
Modifying the value of the cookie key account_type triggers the appearance of a new element on the page. To successfully exploit the bug, we need to supply a value that takes advantage of the loose comparison used by the application (for example, 240610708 -> 0e…).
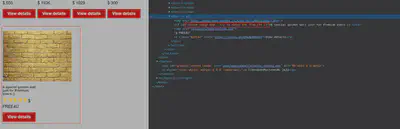
In this new element, there is a comment in which tell us a new endpoint /custom_image.php. In this endpoint, there is a GET parameter we can use to exploit the LFI. The ‘file’ parameter is subject to certain restrictions, including the removal of ‘../’ and a requirement that the file path begin with ‘www/web/images/’. The HTML comment also provides information on which file we should check flag.txt.
# The code I used to exfiltrate
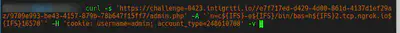
curl -s 'https://challenge-0423.intigriti.io/custom_image.php?file=/app/www/web/images/..\/..\/..\/..\/..\/app/flag.txt' -H 'cookie: username=strange; account_type=240610708' | grep -oP 'base64,.*\">' | sed 's/base64,//g' | sed 's/\">//g' | base64 -d
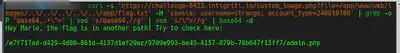
In this file there is a new endpoint /e7f717ed-d429-4d00-861d-4137d1ef29az/9709e993-be43-4157-879b-78b647f15ff7/admin.php. Accessing this endpoint redirects us to the dashboard. Using the LFI, we can download any file of the server. Like for example, the LFI code:
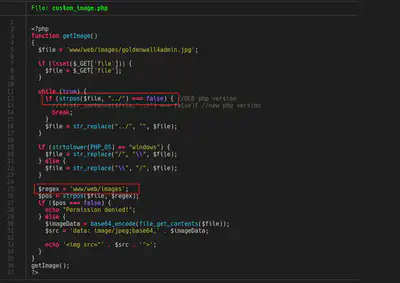
The admin code is in the following image. You can check that we need ‘admin’ value in the cookie ‘username’ and the final bug or challenge we need to exploit (shell_exec).
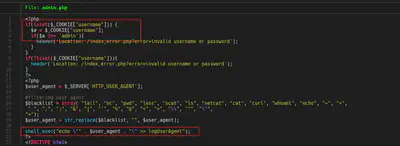
In my case I used the following code to exploit the shell_exec with the user agent to get the flag.
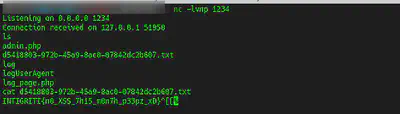
Conclusions
Overall, it was an interesting challenge, although I’m not typically a big fan of black-box challenges. I personally encountered several roadblocks and fell down a few rabbit holes. In any case, I would like to extend my kudos to strangeMMonkey1 for designing this challenging and engaging exercise.
Thanks for reading!